
 The ancient Greek philosopher Heraclitus is credited with the quote, “The only constant in life is change.”
The ancient Greek philosopher Heraclitus is credited with the quote, “The only constant in life is change.”
While Heraclitus was certainly not thinking of cyber security, it couldn't be more true regarding cyber risks.
Cyber risks have become increasingly complex and sophisticated in recent years, making it challenging for businesses to keep up.
We must acknowledge that cyber risks are not just a matter of technology but also a business issue. A single security breach can cause significant financial and reputational damage to an organization. Therefore, it is critical to develop a comprehensive cybersecurity strategy that takes into account the constantly evolving nature of cyber risks.
Many organizations still focus their security priorities on meeting compliance.
This often leaves significant control gaps, as programs designed to satisfy compliance obligations often neglect areas not specifically addressed in the regulation. Other organizations take an ad hoc approach to security that implements controls on an as-needed basis, lacking a coherent strategy.
A more effective option is to adopt a risk-based approach to security based on how the whole business perceives its security risks. Cyber-related risks must be identified, analyzed and prioritized like any other risk an organization might face.
Risk-based approaches to information security allow organizations to adopt strategies that are tailored to their unique operating environment, threat landscape and business objectives.
A Cybersecurity risk management framework also helps organizations to identify their digital assets, their value, and the risks that they are exposed to. A thorough risk assessment helps organizations understand their cybersecurity risk posture and the potential impact of a security breach. This knowledge is critical in making informed decisions about security investments, cybersecurity policies, and resource allocation.
The risk assessment process involves identifying and evaluating potential threats, assessing the likelihood of an attack, and estimating the impact of a security breach. This information is used to prioritize cybersecurity investments and make informed decisions about security policies, procedures, and controls.
Terminology
Risk = Likelihood x Impact
This means that the total amount of risk exposure is the probability of an unfortunate event occurring, multiplied by the potential impact or damage incurred by the event. If you put an euro value on the impact, then you can value the risk and in a simple way compare one risk factor to another.
Risk can also be defined as follows:
Risk = Threat * Vulnerability * Consequence
Risk =Threat * Vulnerability * Asset Value at Risk
Threat – Anything that can exploit a vulnerability, intentionally or accidentally, and obtain, damage, or destroy an asset.
Vulnerability – Weaknesses or gaps in a security program that can be exploited by threats to gain unauthorized access to an asset
Risk – Risk is a function of threats exploiting vulnerabilities to obtain, damage or destroy assets.
Risk assessment methodology
The heart of a risk assessment framework (e.g. ISO27005, NIST SP 800-30, EBIOS Risk Manager, Monarc) is an objective, repeatable methodology that gathers input regarding business risks, threats, vulnerabilities, and controls and produces a risk magnitude that can be discussed, reasoned about, and treated.
The various risk frameworks follow similar structures but differ in the description and details of the steps. However, they all follow the general pattern of identifying assets and stakeholders, understanding security requirements, enumerating threats, identifying and assessing the effectiveness of controls, and calculating the risk based on the inherent risk of compromise and the likelihood that the threat will be realized.
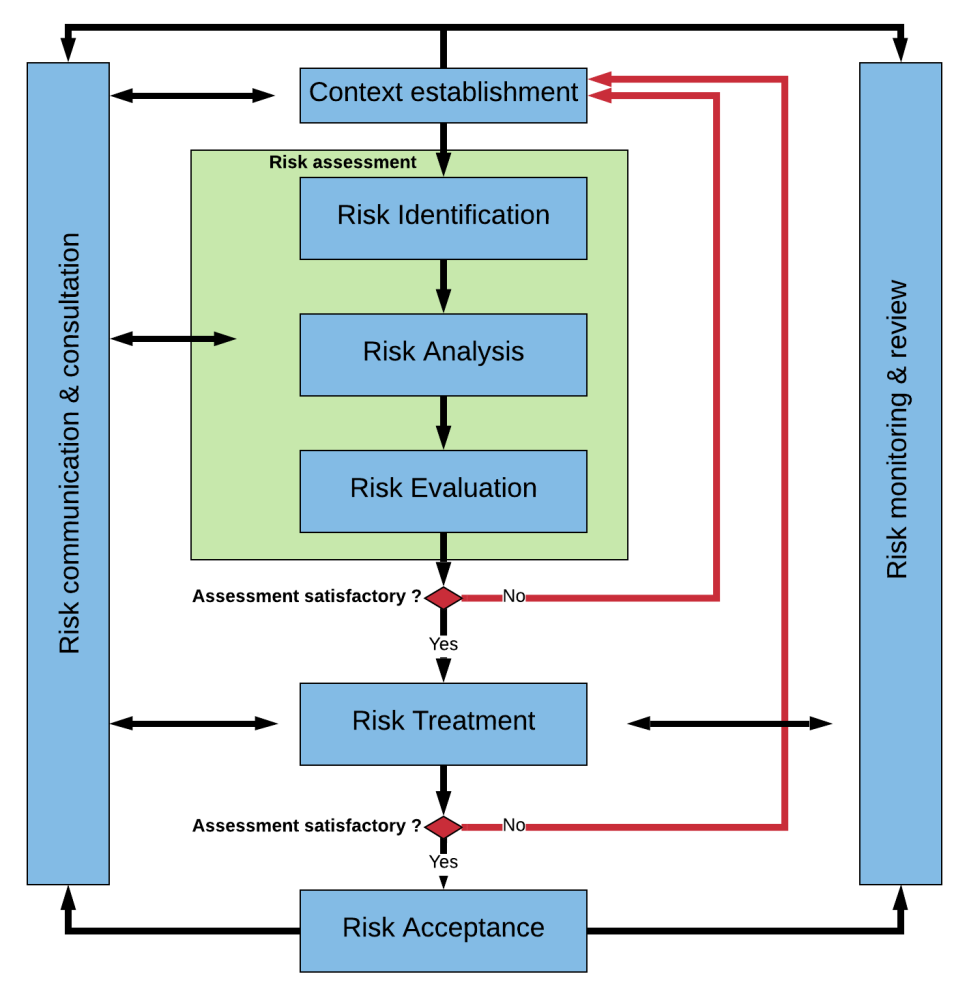
Conducting a cybersecurity risk assessment will allow a business to target its effort on the risks most applicable and impactful to itself.
Make the Move to Risk-Based Security
To learn more about our security solutions, contact us at: philippe.cornette@digisoter.com - www.digisoter.com







